NOTE: This topic applies to Android devices. To configure authentication to Microsoft apps on iOS devices, see Authenticate to Microsoft Apps on iOS devices.
Imprivata Mobile Access Management integrates with Microsoft for automatic sign in and sign out.
- Automatic sign-in.
- Automatic sign-out: Cleanly close all apps supporting the Microsoft Authentication Library (MSAL) and shared device mode.
These benefits save significant time for your workers each day, increase mobile adoption, and remove private data once no longer needed. As a secondary benefit, password management allows your organization to increase password complexity, and increase security, without creating additional burden on your staff.
Requirements
There are strict requirements, which may limit when this feature may be used:
- Microsoft’s apps must be aware of Microsoft’s Shared Device Mode. Supported apps include:
- Microsoft Teams
- Microsoft Outlook
- Microsoft Edge
- Power Apps
- Viva Engage
- Devices must be in Microsoft’s “shared device mode,” which typically requires touching each device to authenticate once as an Azure admin user.
Limitations
- Mobile Access Management supports MSAL-controlled logout with Microsoft Intune configured as corporate-owned dedicated devices with the Managed Home Screen. Fully managed corporate devices cannot be configured with MSAL.
Expected Behavior
On device check out, users will see the standard white Check Out screen with their name. However, this screen now includes a blue button to continue to sign into Microsoft’s authentication system.
- Users open the Microsoft Teams app to complete the sign into Teams. When opened, Teams prompts for a login.
- When the device is returned to the Launchpad, Mobile Access Management automatically signs out of Teams and the Microsoft authentication system with no prompt and no action required by the user.
Microsoft’s Shared Device Mode
Unlike most apps, Microsoft uses device-wide authentication, saving an authentication token. This way, a single sign-in can be shared among multiple apps. Similarly, a single sign-out should cause all apps in the group to be signed out. But Microsoft’s authentication system is generally optimized for 1:1 mobile devices.
To modify these behaviors for shared use, Microsoft has introduced what it calls shared device mode. Microsoft’s shared device mode modifies the Microsoft sign-in workflow to be more suitable for shared devices. In addition, apps can be built to be aware of Microsoft’s shared device mode, and can modify their behavior to be optimized for shared device workflows.
Install and Configure Microsoft Authenticator
Microsoft requires its Authenticator app to be installed to enable shared device mode.
- For Android devices, obtain the Authenticator app from Google Play Store and distribute it to all your shared devices.
- Install Microsoft Authenticator app:
- Open the app and skip all of the blue first user experience screens.
- Click the top menu and select Settings.
- In the Work or school accounts section, click Register your device with your organization.
- Type the username of the Azure Active Directory Device Administrator account.
- Type the password for the user and click Sign in.
- After the device registration process completes, the Authenticator screen displays a message about shared device mode.
- For the pool of shared devices, create an app configuration (AppConfig) for Microsoft Authenticator, with a single key/value pair to enable Microsoft’s shared device mode:
sharedDeviceMode (Boolean) true
- Microsoft Intune: Imprivata recommends that you assign the application configuration to a filtered group. The filter can be set up based on enrollmentProfileName.
- Omnissa Workspace ONE: Change “Boolean” to another type then change it back to work around a UI bug. “True” should be uppercase.
Configure and Deploy Imprivata EAM Profiles
Mobile apps require a profile to feed usernames and passwords from Imprivata Enterprise Access Management (Imprivata OneSign).
Create and deploy EAM application profiles for the Microsoft Authenticator app and other apps on the devices, using the Imprivata Admin Console.
For more information, see Create Imprivata Enterprise Access Management Profiles and Integrate Imprivata Enterprise Access Management.
Sample Android Profile
<!-- Profiles for auto sign in for use with the MSAL library-->
<SSO>
<app nm="com.azure.authenticator" desc="Microsoft Authenticator" profileType="2" appType="0" logoutMethod="0">
<env type="100" nm="Android">
<scn nm="" auto="0" dgs="1">
<!-- Controls 'nm' attributes can be different depenging on the identity provider -
do not forget to replace them with the actual values-->
<ctl nm="i0116" var="USR" />
<ctl nm="i0118" var="PWD" />
</scn>
</env>
</app>
<!-- Microsoft apps integrated with MSAL. To enable MSAL log-out, please set the attribute 'logoutMethod' to "0". -->
<app nm="com.microsoft.teams" desc="Microsoft Teams" profileType="2" appType="0" logoutMethod="0">
<env type="100" nm="Android">
<scn nm="" auto="1" dgs="1">
<ctl nm="com.microsoft.teams:id/edit_email" var="USR" />
<ctl nm="i0118" var="PWD" />
<!-- This control is for clickless sso - add it to fully automate the sign in process-->
<ctl nm="com.microsoft.teams:id/welcome_sign_in_button" action="click" />
</scn>
</env>
</app>
<!-- Microsoft apps not integrated with MSAL -->
<app nm="com.microsoft.office.outlook" desc="Microsoft Outlook" profileType="2" appType="0" logoutMethod="4">
<env type="100" nm="Android">
<scn nm="" auto="1" dgs="1">
<ctl nm="com.microsoft.office.outlook:id/edit_text_email" var="USR" />
<ctl nm="i0118" var="PWD" />
<ctl nm="com.microsoft.office.outlook:id/btn_splash_start" action="click" />
<ctl nm="com.microsoft.office.outlook:id/sso_next_step_button" action="click" test="SKIP" />
<!-- Skipping User Welcome screens -->
<ctl nm="com.microsoft.office.outlook:id/bottom_flow_navigation_start_button" action="click" text="SKIP" />
<ctl nm="com.microsoft.office.outlook:id/product_tour_skip_btn" action="click" text="SKIP" />
</scn>
</env>
</app>
</SSO>
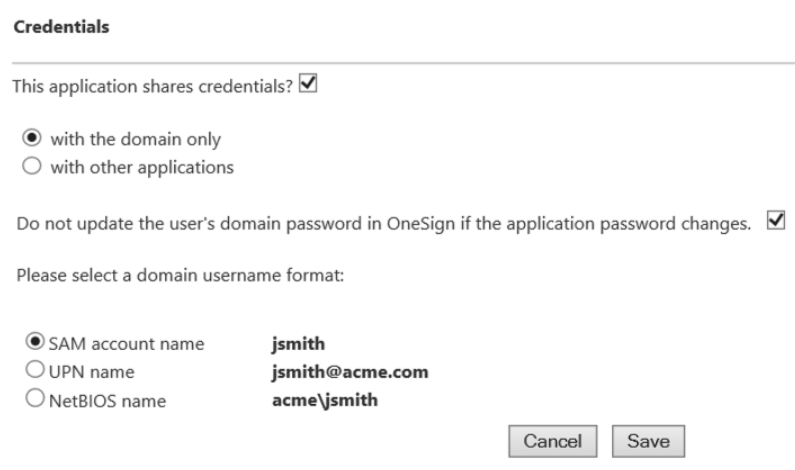
For devices where MSAL-controlled apps and non MSAL-controlled apps are installed on the same device, verify during profile deployment whether the credentials are shared among the apps with the shared credentials store or with the domain.
For more information, see Deploy the Application Profile and Share Credentials.